Shadow (software)
 | |
| Developer(s) | Rynomster, crz, tecnovert |
|---|---|
| Initial release | 19 July 2014 |
| Stable release |
1.5.0.2
|
| Development status | Active |
| Written in | C++ |
| Operating system | Microsoft Windows, OS X, GNU/Linux, Android, iOS |
| Type | Privacy, Anonymity, Decentralized, E-commerce, Encrypted Messaging |
| License | MIT License (Open Source) |
| Website |
shadowproject |
| Shadow | |
|---|---|
| Denominations | |
| Subunit | |
| 0.001 | mSDC (millicoin) |
| 0.000001 | µSDC (microcoin) |
| 0.00000001 | Shadowshi |
| Plural | ShadowCash |
| Symbol | SDC |
| Demographics | |
| Date of introduction | 19 July 2014 |
| User(s) | Worldwide |
| Issuance | |
| Administration | Decentralized |
| Valuation | |
| Supply growth | Approximately 6.4 million coins maximum, with a 2% annual inflation rate. |
Shadow (SDC[1]) is a peer-to-peer privacy platform, created under an open source license, featuring a built-in cryptocurrency, end-to-end encrypted messaging and E-commerce. The decentralized network aims to provide anonymity and privacy for everyone through a simple user-friendly interface by taking care of all the advanced cryptography in the background. ShadowCash was created as the de facto currency for the peer-to-peer decentralized ShadowMarket (currently under development). The project began in July 2014 as a fork of Bitcoin (BTC) engineered to enhance the bitcoin protocol by adding dual-key stealth addresses and traceable ring signatures[2] for increased transactional anonymity.
ShadowCash consensus is based on an open source protocol known as Proof-of-stake (PoSv3) and is not managed by any central authority, the network regulates itself.[3]
Decentralized marketplace

The main component of the Shadow platform is the decentralized marketplace dubbed 'ShadowMarket'. The decentralized nature of the network makes it very resilient against shutdown attempts and permits for anyone to participate in a true free market without the possibility of interference or eavesdropping by malicious parties. Every node in the network distributes and stores all the open market listings, to prevent bloating the network with outdated and incorrect listings, each one must contain an expiration date and the appropriate listing fee must be paid. The blockchain-like mechanism for storing the listings is a technique called Private Information Retrieval and is key to preserving the anonymity and privacy of both the vendor and possible buyer(s).
Two-party smart escrow
The smart escrow system is devised so neither party can profitably defraud the other party without risk. It is based on mutual assured destruction (MAD): The buyer risks twice the amount required for purchase and the vendor risks the purchase price plus the item that they ship. These funds are locked in a 2-of-2 multisignature address and can only be released when both parties agree and sign the transaction. If they can't agree before a certain expiration date, the funds stay locked indefinitely and the address becomes unspendable. The expiration date is extendable if both parties agree to send the transaction to yet another 2-of-2 multisignature address with a new expiration date.
A new opcode CHECKLOCKTIMEVERIFY (CLTV) is implemented to enable the mutual assured destruction, more about the technical specifications of this improvement can be found on the BIP65 github page. Shadow uses a different escrow model than proposed in BIP65, instead we drop both keys when the expiration is reached, essentially destroying the funds.
Mutual assured destruction (MAD)

This strategy finds its roots in the Ultimatum Game, a well known economic experiment in the field of game theory. The key difference between Shadows escrow and the Ultimatum Game is that negotiations are possible in the form of refunds. The payoff matrix exemplifies all the scenarios without the possibility of refund.
Bad buyer.
If the buyer receives the item and decides not to finalize the transaction then the address becomes unspendable after the expiration date and neither party gets their insurance deposit back. The buyer will have effectively paid twice the price but the vendor loses his insurance deposit and the item.
Bad vendor.
The vendor does not to ship the item, leaving the buyer with the option to finalize the transaction or not: finalizing the transaction causes him to minimalize his losses to one time the price of the item and the vendor makes a profit of one time the item price. If the buyer decides not to finalize the transaction he loses twice the amount of the item price but also causes the vendor to lose his insurance deposit. The buyer is to some extent at a disadvantage and motivated to finalize the transaction to minimize his loses in case of a vendor scam. Both the buyer and the vendor will be motivated to extend the escrow transaction and work towards a refund agreement that both parties are willing to sign.
Why not use escrow agents then?
Because this brings a middleman into the equation which is no means of fairly solving disputes. It is still the buyers word against the vendors. A delivery receipt does not always mean the correct item was received.
What if the item was lost in the mail?
The buyer will have to convince the vendor that he didn't receive the item and both parties must come to a refund agreement that both parties are willing to sign. The vendor may believe the buyer if they have a good history of transactions. If the vendors thinks you are trying to scam them then he might decide to not deal with you again and you lose your insurance deposit and the vendor loses once the item price and the item lost in the mail.
Reputation
While two-party escrow with Mutual Assured Destruction is a viable way to prevent most frauds and scams from being profitable, it is not a perfect solution on itself. This is where the reputation system steps in to complement the ecrow system. Each vendor will have a reputation which reflects the (dis)satisfaction of his clients based on their interactions with the vendor.
The scheme on which the reputation will be based in unknown but there has been speculation about the usage of EigenTrust++,[4] an improved version of the peer-to-peer reputation scheme named Eigentrust.
Listing fees
The listing fee, charged for each market listing, is 0.2 SDC per 4KB per 2 days, so posting a 4KB listing for 4 days will be 0.4 SDC, just as an 8KB ad for 2 days will be 0.4 SDC. Updates to marketplace listings will cost 0.05 SDC and will not add any duration to the listing.
Encrypted messaging
The encrypted messaging dubbed ShadowChat is a vital part of the project, it allows for secure and reliable communications that can't be blocked because of the decentralized nature. It opens the door for developers to build secure applications on without having to deal with any complex cryptography. The first application will be the decentralized marketplaces, but Shadow is also able to run on systems suchs as the Raspberry Pi opening the door to the Internet of Things, the possibilities are endless.
Message propagation

Encrypted messages are stored on every participating node of the network, this prevents adversaries from uncovering the recipient of an encrypted message through network trafiic analysis. The messages are grouped by time in divisions of one hour, each group is called a bucket. The image shows how these buckets are synchronised across the network.
Key sharing
The message protocol utilizes the Elliptic Curve Diffie-Hellman (ECDH) key exchange method for generating a secret key, this allows for sending messages without needing both parties to be online.
Cryptocurrency
Blockchain
The blockchain is a public ledger that records transactions. A novel solution accomplishes this without any trusted central authority: maintenance of the blockchain is performed by a network of communicating nodes running the software. Transactions of the form payer X sends Y bitcoins to payee Z are broadcast to this network using readily available software applications. Network nodes can validate transactions, add them to their copy of the ledger, and then broadcast these ledger additions to other nodes. The blockchain is a distributed database; to achieve independent verification of the chain of ownership of any and every bitcoin (amount), each network node stores its own copy of the blockchain. Approximately sixty times per hour, a new group of accepted transactions, a block, is created, added to the blockchain, and quickly published to all nodes. This allows shadowcash software to determine when a particular amount has been spent, which is necessary in order to prevent double-spending in an environment without central oversight. Whereas a conventional ledger records the transfers of actual bills or promissory notes that exist apart from it, the blockchain is the only place that shadowcash can be said to exist in the form of unspent outputs of transactions.
Consensus
Consensus in a decentralized digital currency like Bitcoin is achieved by requiring generated blocks to contain a proof that the node which generated the block solved a computational hard task. Unfortunately the concept of the Proof-of-Work (PoW) based system tends to lean towards eventual selfdestruction. ShadowCash uses Proof-of-stake (PoS) which aims to replace the way of achieving consensus in a distributed system; instead of solving the Proof-of-Work, the node which generates a block has to provide a proof that it has access to a certain amount of coins before being accepted by the network. Generating a block involves sending coins to oneself, which proves the ownership. The required amount of coins (also called target) is specified by the network through a difficulty adjustment process similar to PoW that ensures an approximate, constant block time. As in PoW, the block generation process will be rewarded through transaction fees and a supply model specified by the underlying protocol; which can also be seen as interest rate by common definition.[5]
Tokens
A system of tokens has been introduced by the developers because the cryptography behind the privacy enhancing features of ShadowCash require a signing scheme that is different from normal Bitcoin transactions. The signing scheme is a cryptographic computation used to prove ownership of a certain amount coins. In simplified language, the way you prove others that you own a certain amount of money on the blockchain is different for private transactions. Thus a clever system has been implemented that allows for a transaction to happen in the normal, public circuit or in the private system. When a private transaction is created it contains an ANON_MARKER in the ScriptSig to tell the nodes to use the privacy enhanced scheme instead of the normal public scheme. You can freely switch coins from the public to the private circuit and the other way around without a third party through a simple SDC to SDT or SDT to SDC transaction.
Public (SDC)
ShadowCash was built on a fork of bitcoin thus inheriting its structure of blockchain, transaction handling and all other components. The public currency named shadowcash has exactly the same technical structure and properties as the bitcoin currency. Sending and receiving SDC is not anonymous and the trail is not obfuscated.
Private (SDT)
Private shadowtokens are not very different from the public currency, the only difference is the digital signature.necessary for proving ownership. The signature is constructed in such a way that the original transaction to the sender is obfuscated by X amount of other transactions. Therefore, it is not clear which transaction was spent. Along with the unknown state of a transaction comes the double-spending problem thus a different technique had to be applied to prevent the traditional double-spending attempts.
Ownership
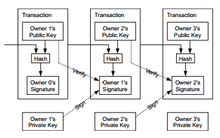
Ownership of shadowcash (SDC) implies that a user can spend the shadowcash associated with a specific address. To do so, a payer must digitally sign the transaction using the corresponding private key. Without knowledge of the private key, the transaction cannot be signed and bitcoins cannot be spent. The network verifies the signature using the public key. If the private key is lost, the shadowcash network will not recognize any other evidence of ownership; the coins are then unusable, and thus effectively lost.
Ownership ShadowTokens (SDT)
Proving ownership of shadowtokens uses a different cryptographic scheme to sign and verify the transaction. It is only possible to spend a shadowtoken upon digitally signing the transaction using a traceable ring signature.
Traceable ring signatures
The combination of two cryptographic techniques: ring signatures and non-interactive zero-knowledge proofs is what makes up the traceable ring signatures. It is a special form of ring signature because each one is tagged with a keyImage, a hash of the private key being spent.
Ring signatures

A ring signature is a type of digital signature that can be performed by any member of a group of users that each have keys. Therefore, a message signed with a ring signature is endorsed by someone in a particular group of people. One of the security properties of a ring signature is that it should be computationally infeasible to determine which of the group members' keys was used to produce the signature. Ring signatures are similar to group signatures but differ in two key ways: first, there is no way to revoke the anonymity of an individual signature, and second, any group of users can be used as a group without additional setup. Ring signatures were invented by Ron Rivest, Adi Shamir, and Yael Tauman, and introduced at ASIACRYPT in 2001.[6] The name "ring signature" comes from the ring-like structure of the signature algorithm.
The members of the ring signatures used to spend a ShadowToken are the public keys of other ShadowTokens of the same denomination. Therefore, nobody except the sender knows exactly which token was spent, not even the receiver of the transaction.
Key Image
The key image is what gives the ring signature it's double spend prevention property. If a new ring signature would be submitted to the network, the key image would be the same as the previously spent ring signature. The key image is derived from the secret key being spent when creating a ring signature. It's extremely important and crucial to maintain anonymity that the elliptic point returned by the keyimage is one that is indifferentiable hashed to an elliptic point. [7]
Non-interactive zero knowledge proofs
A non-interactive zero-knowledge proof [8] is a method by which one party (the prover) can prove to another party (the verifier) that a given statement is true, without conveying any information apart from the fact that the statement is indeed true. The non-interactive zero-knowledge proof used is ring signature.
Dual-key stealth addresses
These address are different from the standard addresses commonly used in cryptocurrencies and allow for better privacy. A dual-key stealth address can be shared publicly by the recipient yet any transaction made out to this address can not be linked back to it. When the stealth address has been revealed to the payer(s), it will be enable the payee to receive infinite unlinkable payments. Meaning that each payment to a Stealth address computes a new unused normal address on which the funds ought to be received, any eavesdropper will be unable to link the two addresses.
They play an important role in SDT transactions, but are not limited to SDT and thus can also be used for SDC transactions
The original visionaries were the creators of Bytecoin.
More of the technical details about dual-key stealth addresses can be found on the documentation website.
Anonymity
Tor
The software is fully compliant with Tor, installation instructions can be found in the documentation. It is highly advised to run a hidden service to maintain the decentralization and better anonymity.
Invisible Internet Project (I2P)
I2P support is on its way.
Exchanges
- Bittrex.com - https://www.bittrex.com/Market/Index?MarketName=BTC-SDC
- Poloniex - https://poloniex.com/exchange#btc_sdc
- ShapeShift - https://shapeshift.io/
- Exchanged.i2p - I2P Hidden service exchange - http://exchanged.i2p/
See also
Development
(Ongoing work and projects)
Shadow software, provides a set of tools for decentralised eCommerce.
- ShadowCore is the client/server application which allows use of subsequent applications
- ShadowCash is a privacy-focused[9] cryptocurrency based on blockchain technology that forms the backbone of the main decentralised network
- ShadowSend is an integrated Cryptocurrency tumbler-like service for anonymising coin transactions[10]
- ShadowChat is an encrypted chat function running over a separate network
- ShadowMarket - Yet to be launched is marketplace suitable for darknet markets and similar[11]
External links
References
- ↑ "ShadowCoin chart". bittrex.com. Retrieved 2015-07-22.
- ↑ "ShadowCash: Zeroknowledge Anonymous Distributed ECash via Traceable Ring Signatures" (PDF). Retrieved 2015-07-22.
- ↑ Satoshi, Nakamoto. "Bitcoin: A Peer-to-Peer Electronic Cash System" (PDF). Bitcoin.org. Retrieved 24 April 2013.
- ↑ "EigenTrust++ White paper" (PDF). EigenTrust++. Xinxin Fan, Ling Liu, Mingchu Li and Zhiyuan Su. Retrieved 21 January 2015.
- ↑ "BlackCoin: Proof of Stake v2" (PDF).
- ↑ Rivest, Ronald L.; Shamir, Adi; Tauman, Yael (2001-12-09). Boyd, Colin, ed. How to Leak a Secret. Lecture Notes in Computer Science. Springer Berlin Heidelberg. pp. 552–565. ISBN 9783540429876.
- ↑ "ge_fromfe_writeup" (PDF).
- ↑ "Succinct Non-Interactive Zero Knowledge for a von Neumann Architecture" (PDF). Eli Ben-Sasson, Alessandro Chiesa, Eran Tromer and Madars Virza.
- ↑ Gupta, Nikhil (29 March 2015). "Need Something More Anonymous Than Bitcoin? Try ShadowCash!". Retrieved 4 July 2015.
- ↑ DeepDotWeb (28 January 2015). "Shadowcash Hits Zero-Knowledge Jackpot with Casino-style Anonymity". Retrieved 4 July 2015.
- ↑ Cox, Joseph (23 March 2015). "The Race for a Decentralised Silk Road Is On". Retrieved 4 July 2015.